Article -> Article Details
| Title | Social Engineering Attacks: How to Spot and Avoid Them? |
|---|---|
| Category | Computers --> Security |
| Meta Keywords | cybersecurity coe, centre of excellence hyderabad, cyber security hyderabad, cyber security telangana, Cybersecurity Incubation centre, Cybersecurity Academia and R&D Centres, cloud computing vs cyber security, cyber security challenges in india |
| Owner | Cybersecurity |
| Description | |
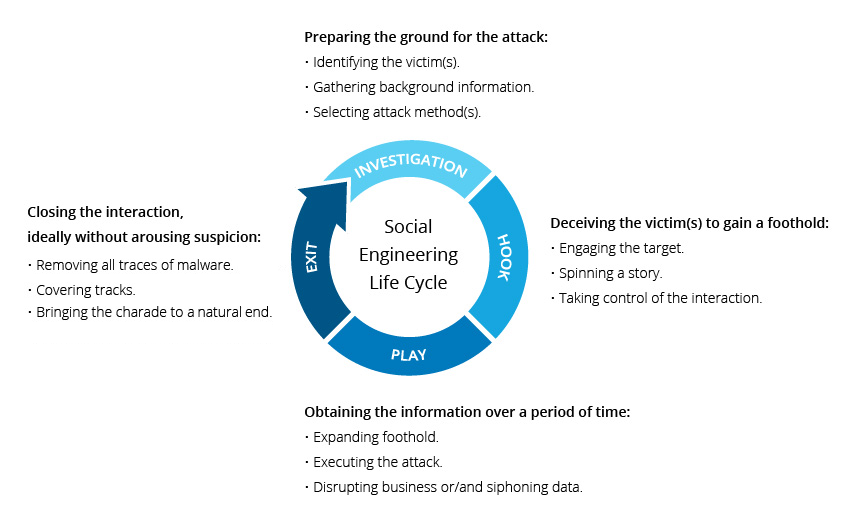
| The internet has become the lifeblood of every individual and business in this disrupting digital world, triggered by the pandemic. Organizations have been forced into changing their working practices with a majority of them establishing remote work or Work from Home (WFH) for their employees. This unexpected switch has seen a massive spike in cyberattacks and hackers are seizing every opportunity to take advantage of the situation. Hacktivists are stepping up their cybercriminal activities by exploiting human psychology to trick individuals into handing over valuable personal and company data. They are utilizing “social engineering” to commit high-value cybercrimes. Although the pandemic is certainly not the first occurrence of such attacks, this phase has brought them into the mainstream of sophisticated cyber threatscape. According to KnowBe4, only about 3% of malware tries to exploit an exclusively technical flaw. The other 97% instead targets users through Social Engineering. What is Social Engineering? In simple terms, social engineering is the act of deceiving or manipulating someone into divulging confidential or personal information that may be used for malicious activities. Attackers use social engineering tactics to exploit people’s natural tendency to trust others. Such attacks rely heavily on human interaction, and they are all about the ‘psychology of persuasion’. The attacker fabricates a false sense of security and trust with the unsuspecting users or employees, then encourages them into taking unsafe actions. For this reason of human manipulation, it is also considered ‘human hacking’. Many social engineering attacks exploit basic human cognitive functions like people’s willingness to be helpful, curiosities to experience new things, fears, etc. Social engineering attackers are called social engineers. Their physiological tricks can break the strength of even the best security systems. How Does a Social Engineering Attack Work? This simple figure illustrates the typical lifecycle of a social engineering attack:
Common Social Engineering Attacks Almost all cyberattacks, where human interaction is involved, have some form of social engineering in them. According to Verizon’s 2021 Data Breach Investigations Report, 85% of breaches involved the human element, while social engineering was an integral part of 35% of those incidents. Here we enlist the most popular social engineering attack techniques:
How to Spot a Social Engineering Attack? The approach of social engineering attacks varies for every victim and is primarily based upon the attacker’s goals and the kind of information that can be extracted. The following section lists common, recognizable clues of a social engineering attack.
These are some of the prevalent red flags of a social engineering attack that one should watch out for. One needs to be on their toes when reading through emails and messages. How to Avoid a Social Engineering Attack? Since social engineering attacks are devised to leverage natural human traits like fear, curiosity, greed, respect, desire to help, etc., these security threats will never vanish no matter how robust a security system you have in place. They, however, can be substantially prevented by taking proactive ways. Following tips can help improve your protection against a social engineering attack:
Conclusion Social engineering attacks exploit human psychology and can wreak havoc on our devices and data. Social engineers are increasingly using sophisticated tactics to manipulate the human mind to commit these cybercrimes. Thus, without a doubt, social engineering attacks are bound to thrive with our growing digital footprint. While there is no permanent cure to a social engineering attack, by being fully aware of how it works and taking basic safety measures, we will be less likely to fall victim to such grievous cyberattacks. References: | |